Mastering Conditional Access Policies: The Backbone of Dynamic Security in Azure
In today’s dynamic and increasingly remote digital environment, securing organizational resources is more challenging than ever. Identity management must move beyond simple passwords and evolve to dynamically control access based on various factors. Azure Conditional Access Policies (CAP) offer an adaptive security solution that enables businesses to enforce access controls based on real-time signals like user behavior, device health, and location.
This detailed guide covers everything you need to know about Azure Conditional Access Policies, including key features, real-world use cases, and a step-by-step guide on how to implement Conditional Access for enhanced security.
What Are Azure Conditional Access Policies?
Conditional Access Policies in Azure are security measures designed to control access to corporate resources based on specific conditions. By dynamically enforcing access based on real-time context, Conditional Access helps protect your organization’s data from unauthorized access while ensuring legitimate users experience minimal disruptions.
The policies evaluate various signals (user location, device compliance, sign-in risks, etc.) and then apply controls (such as requiring Multi-Factor Authentication or blocking access) to mitigate potential risks.
Why Are Conditional Access Policies Critical?
In an era where remote work and cloud-based applications are the norm, traditional security measures often fall short. Conditional Access Policies address these gaps by enforcing security dynamically. Here’s why they are essential:
- Reduce identity-based attacks by blocking risky access attempts.
- Enforce MFA or other security controls only when necessary to maintain a balance between user experience and security.
- Comply with regulatory requirements for secure access to sensitive data and applications.
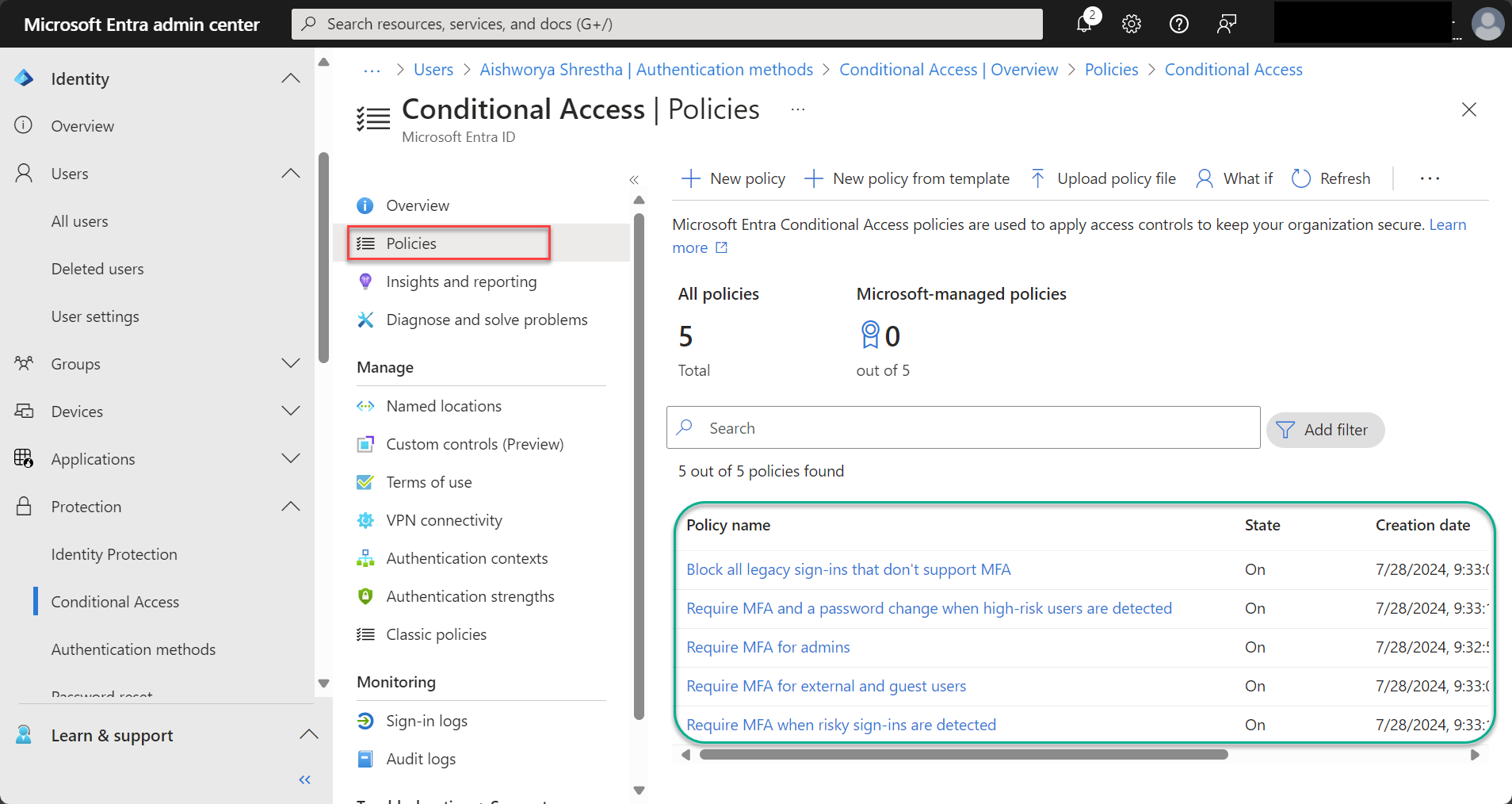
How Azure Conditional Access Policies Work
Azure Conditional Access operates on an if-then logic: If specific conditions (signals) are met, then the system applies certain access controls. Here’s how it works:
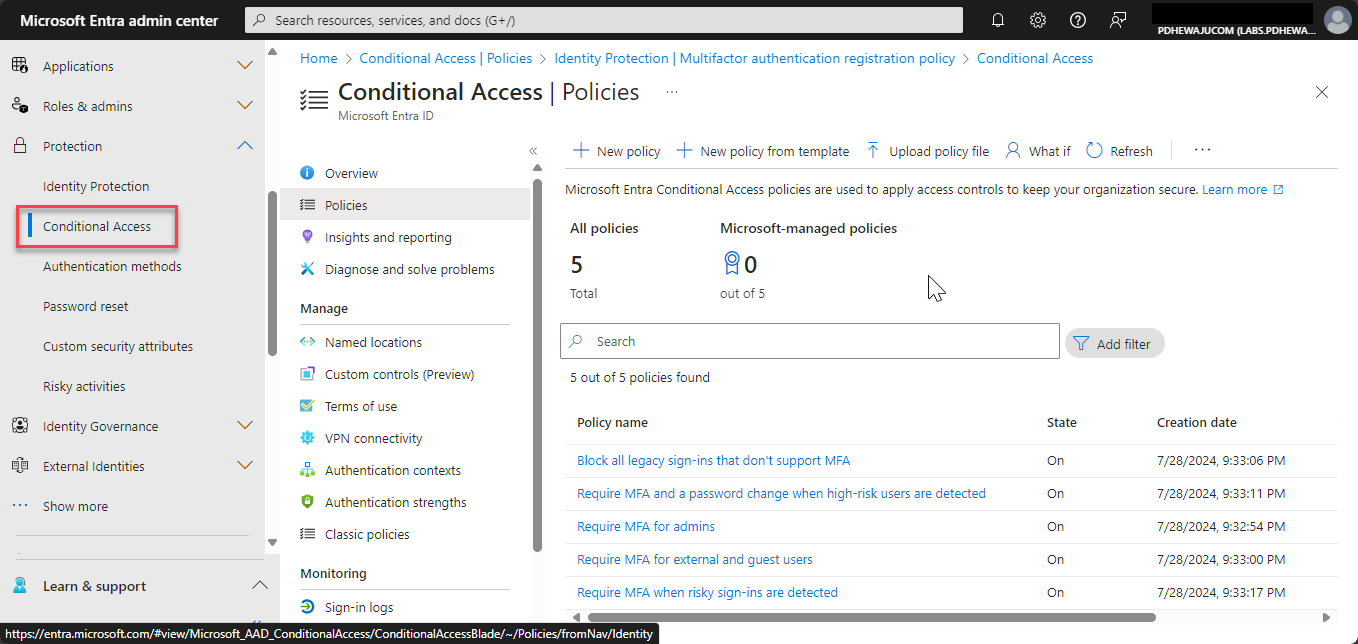
1. Signals (Conditions)
- User/group membership: Policies can apply to specific users or groups within your organization.
- Named Location: Control access based on user location (e.g., block or allow specific geographic regions). You can add Countries, IP ranges and Trusted IP on Named location to filter access of your users.
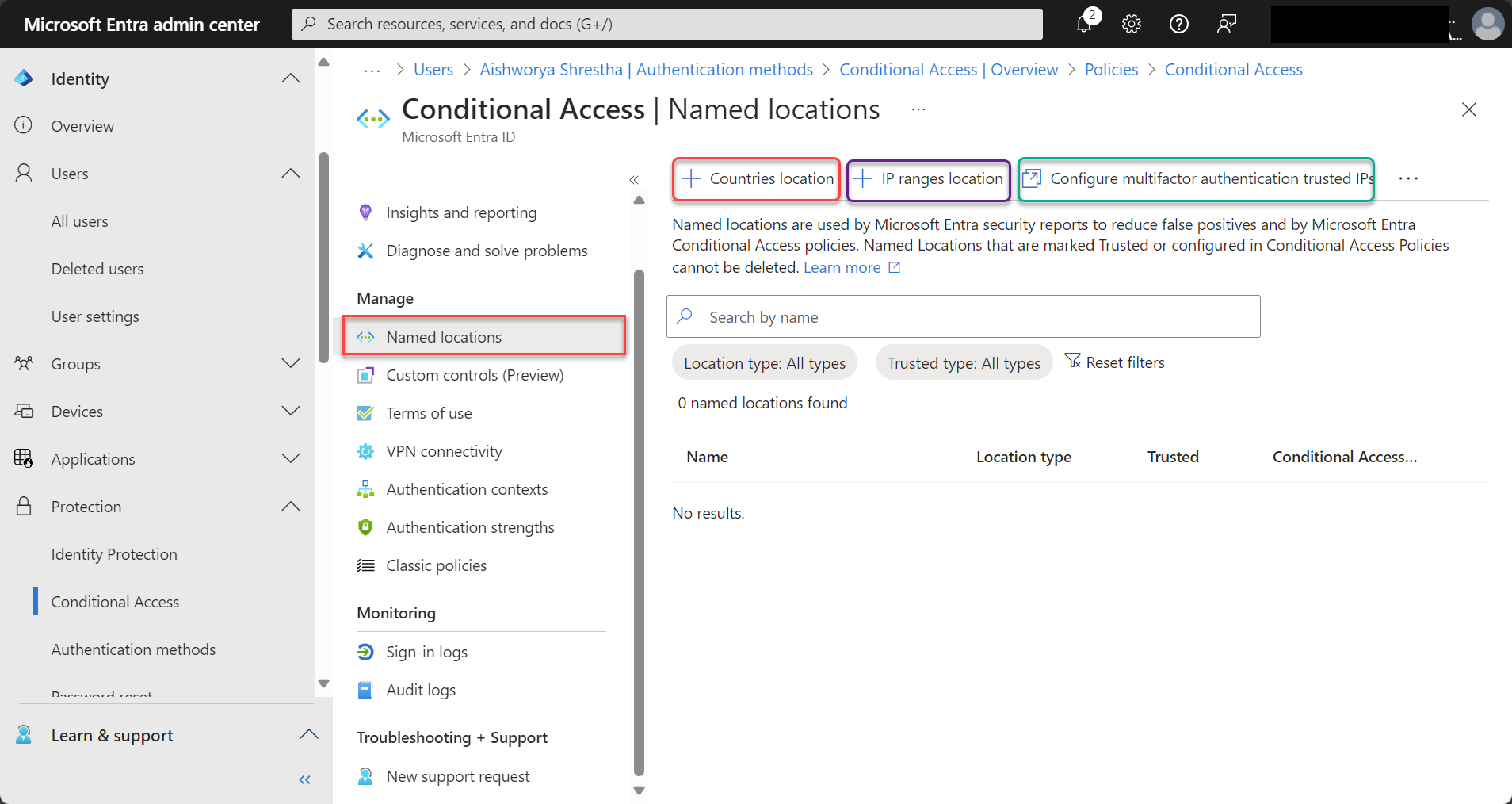
- Device compliance: Ensure only trusted devices (e.g., compliant with security policies) can access resources.
- Application: Apply policies to specific applications (e.g., higher security for HR or financial apps).
- Sign-in risk: Azure detects risky sign-ins (like unusual IP addresses or compromised credentials) and adjusts access controls accordingly.
2. Controls (Actions)
- Grant Access: Conditional Access can allow access under specific conditions, such as requiring MFA, ensuring device compliance, or using trusted networks.
- Block Access: Restrict access entirely based on predefined risk factors.
- Session Controls: Manage session duration, enforce app policies, or restrict data access within applications.
Key Features of Azure Conditional Access Policies
1. Granular Access Controls
Conditional Access Policies offer fine-grained control over who can access your resources, from where, and under what conditions.
2. Adaptive MFA Enforcement
Conditional Access integrates with Multi-Factor Authentication (MFA), applying it only when necessary. This ensures a balance between security and user convenience.
3. Real-Time Threat Detection
Conditional Access can dynamically adjust access policies in real-time by evaluating risks like suspicious login behavior or non-compliant devices.
4. Detailed Reporting
Azure provides robust reporting and monitoring tools to help you track access attempts, policy effectiveness, and potential security gaps.
5. Risk-Based Controls
Conditional Access works with Azure Identity Protection to assess sign-in risks and apply security measures based on the level of threat detected.
Step-by-Step Guide: How to Implement Azure Conditional Access Policies
Implementing Conditional Access Policies in Azure involves a few key steps to ensure you are maximizing security without compromising user productivity.
Step 1: Define Your Use Cases and Security Goals
Before you start configuring policies, identify your organization’s use cases and security objectives. For example:
- Do you want to enforce MFA for remote workers?
- Do you want to block access from certain countries or regions?
- Should critical applications (HR or finance) have stricter controls than others?
Step 2: Access Azure AD and Navigate to Conditional Access
- Go to the Azure portal (https://portal.azure.com/).
- In the left-hand navigation, select Azure Active Directory.
- Under Protection, select Conditional Access.
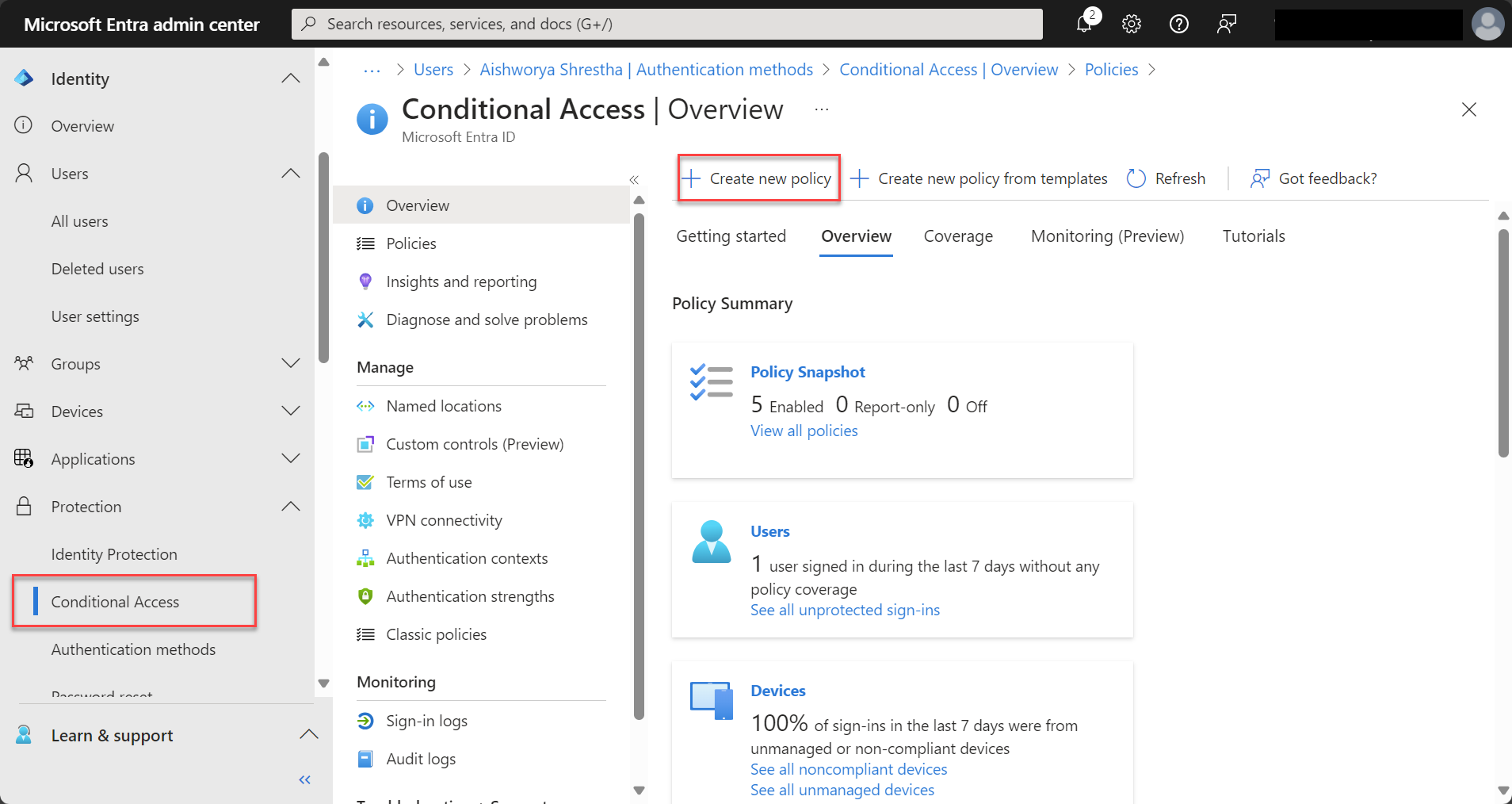
Step 3: Create a New Conditional Access Policy
- Select Create New Policy.
- Name your policy (e.g., “Restrict_Sample_Policy” or “Block Untrusted Locations”).
Step 4: Define the Policy Conditions (Signals)
Under the Assignments section, you can define the specific conditions that will trigger the policy:
- Users and Groups: Select the specific users or groups this policy will apply to (e.g., only remote workers, admins, or everyone). Here in my case, I have applied to all users in my organization excluding only few users.
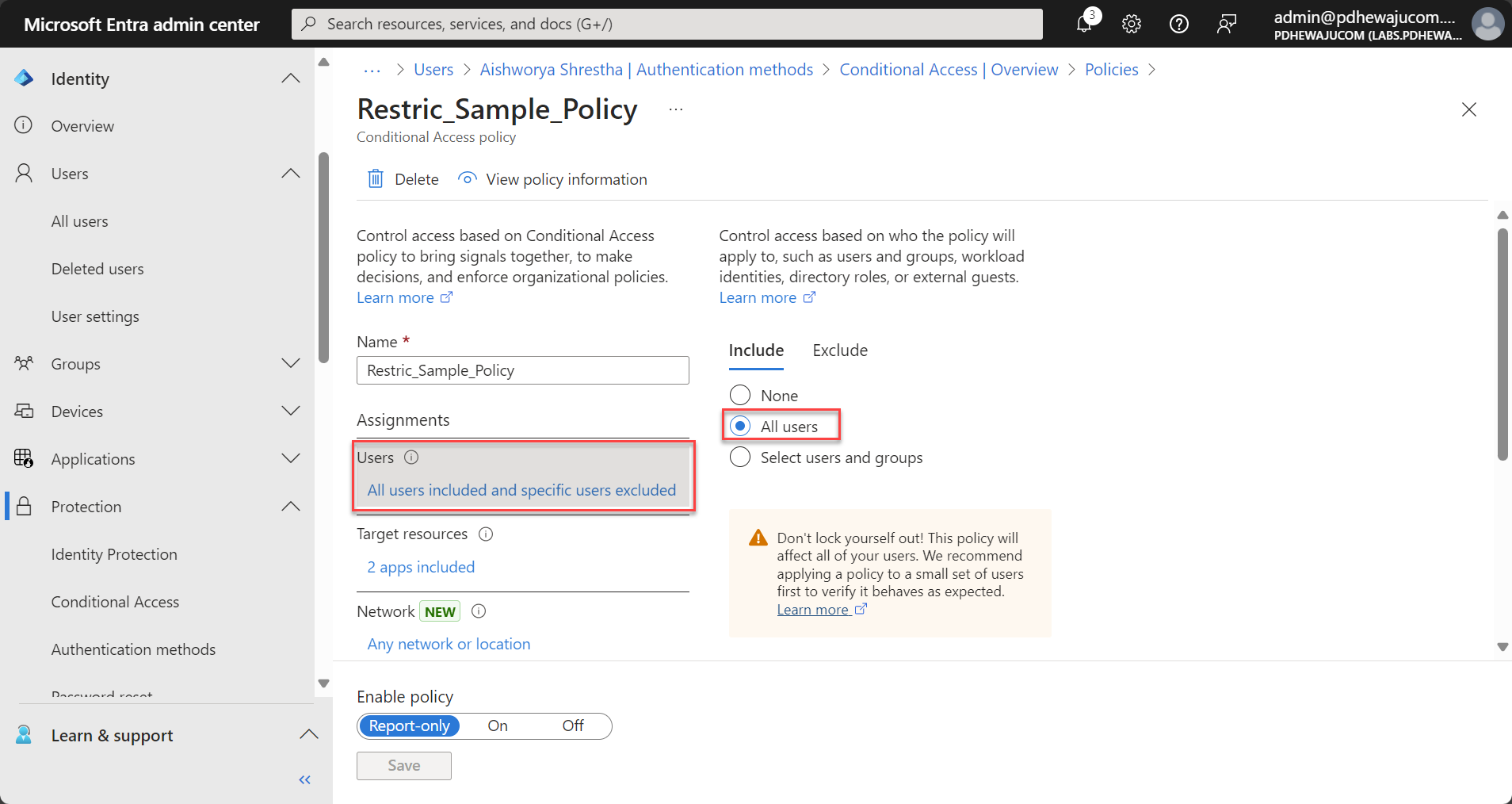
- Cloud Apps: Choose the apps to which this policy will apply. For example, apply stricter controls to sensitive apps like Office 365, HR systems, or financial applications. Here in snapshot, I have select inbuild application of M365 – Office 365 exchange online and my 3rd Party SSO integrated application.
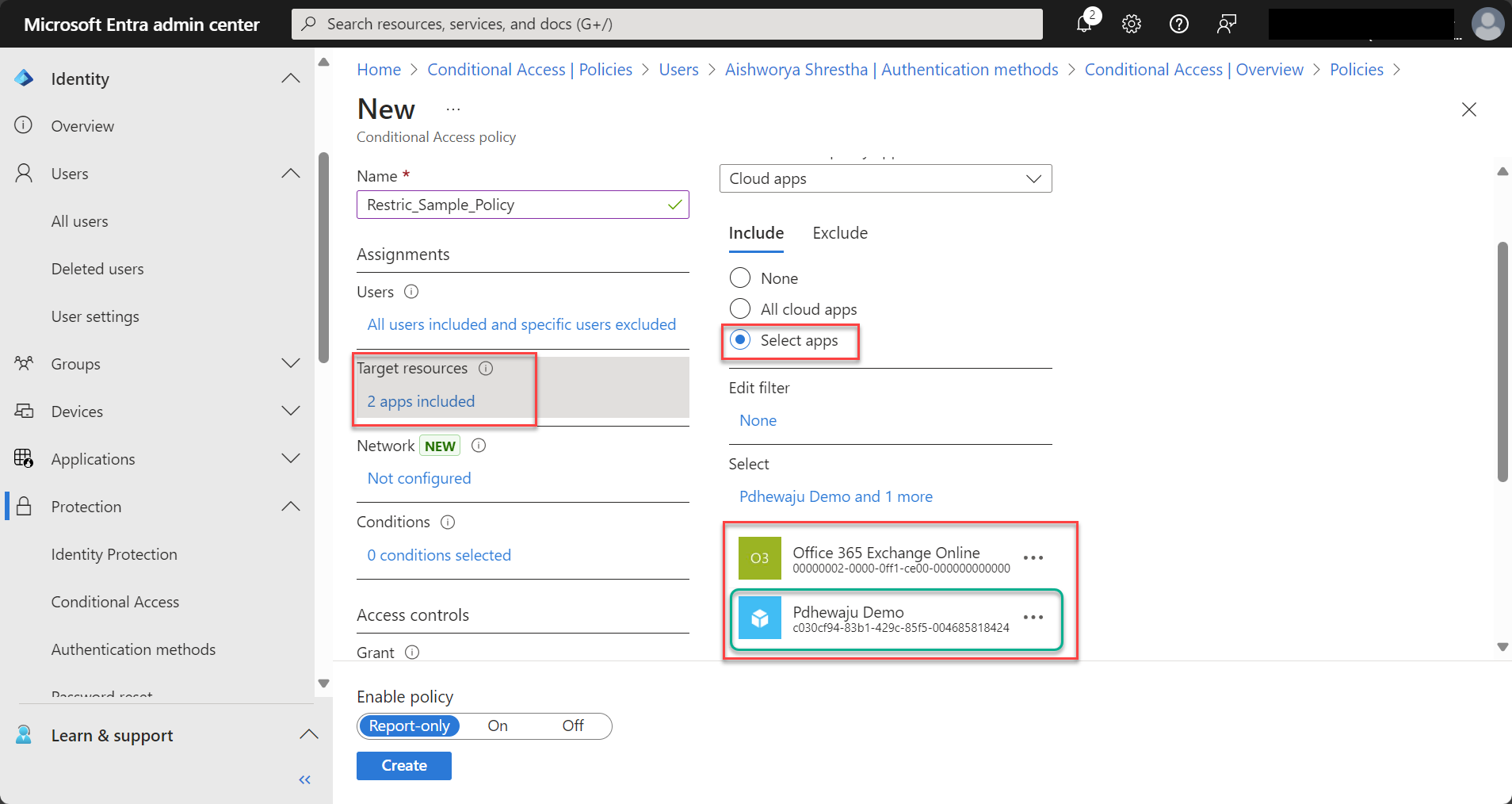
- Conditions: Define additional conditions such as:
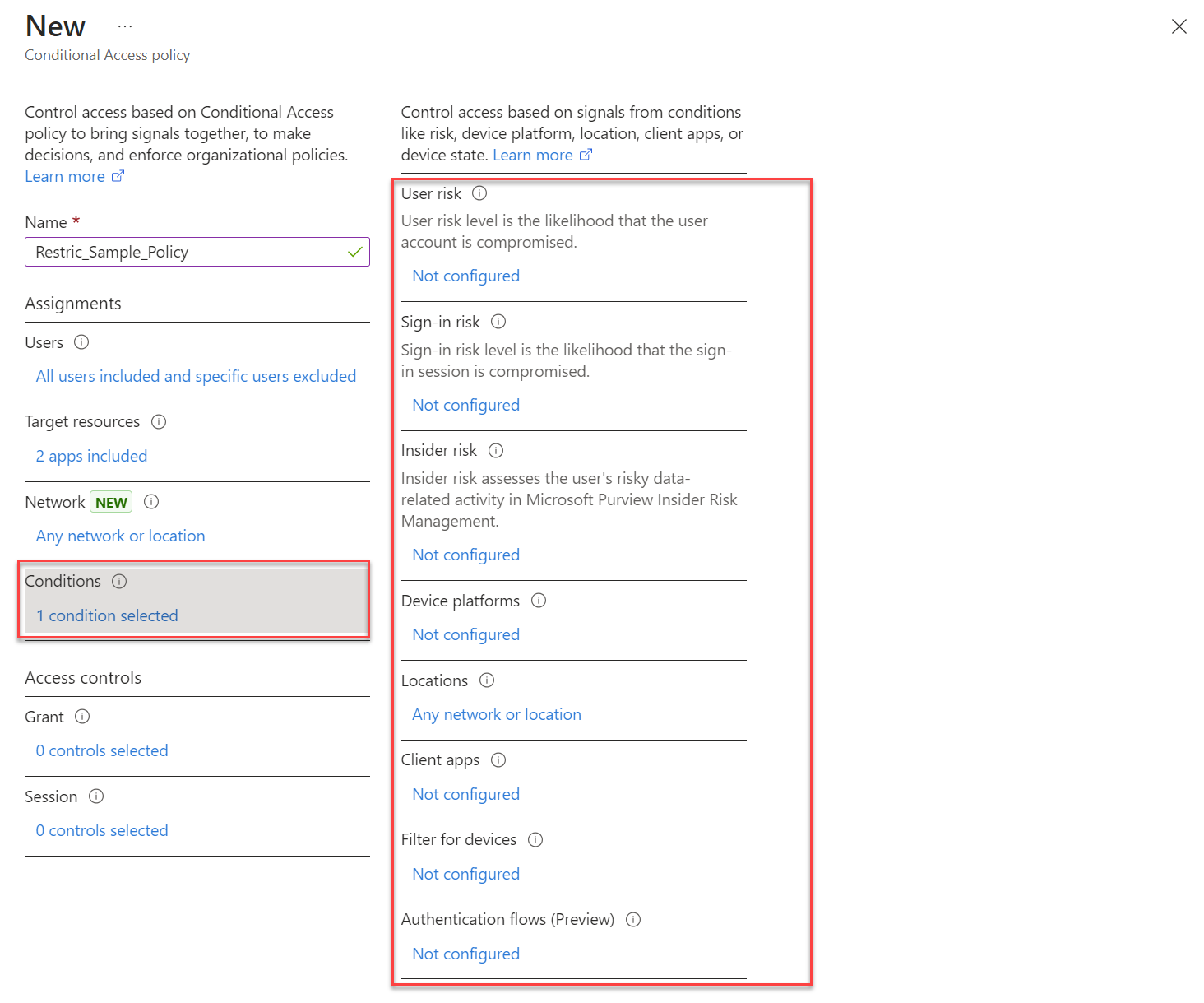
-
- Sign-in Risk: Apply the policy based on risk levels like low, medium, or high-risk sign-ins.
- Device Platforms: Apply policies to specific device types (Windows, macOS, Android, iOS).
- Locations: Restrict or allow access based on geographic location or IP ranges.
- Device State: Ensure only compliant devices can access resources.
Step 5: Define Access Controls (Actions)
In the Access Controls section, choose what actions will be triggered when the conditions are met:
- Grant Access: Allow access under specific conditions like requiring MFA, device compliance, or password change.
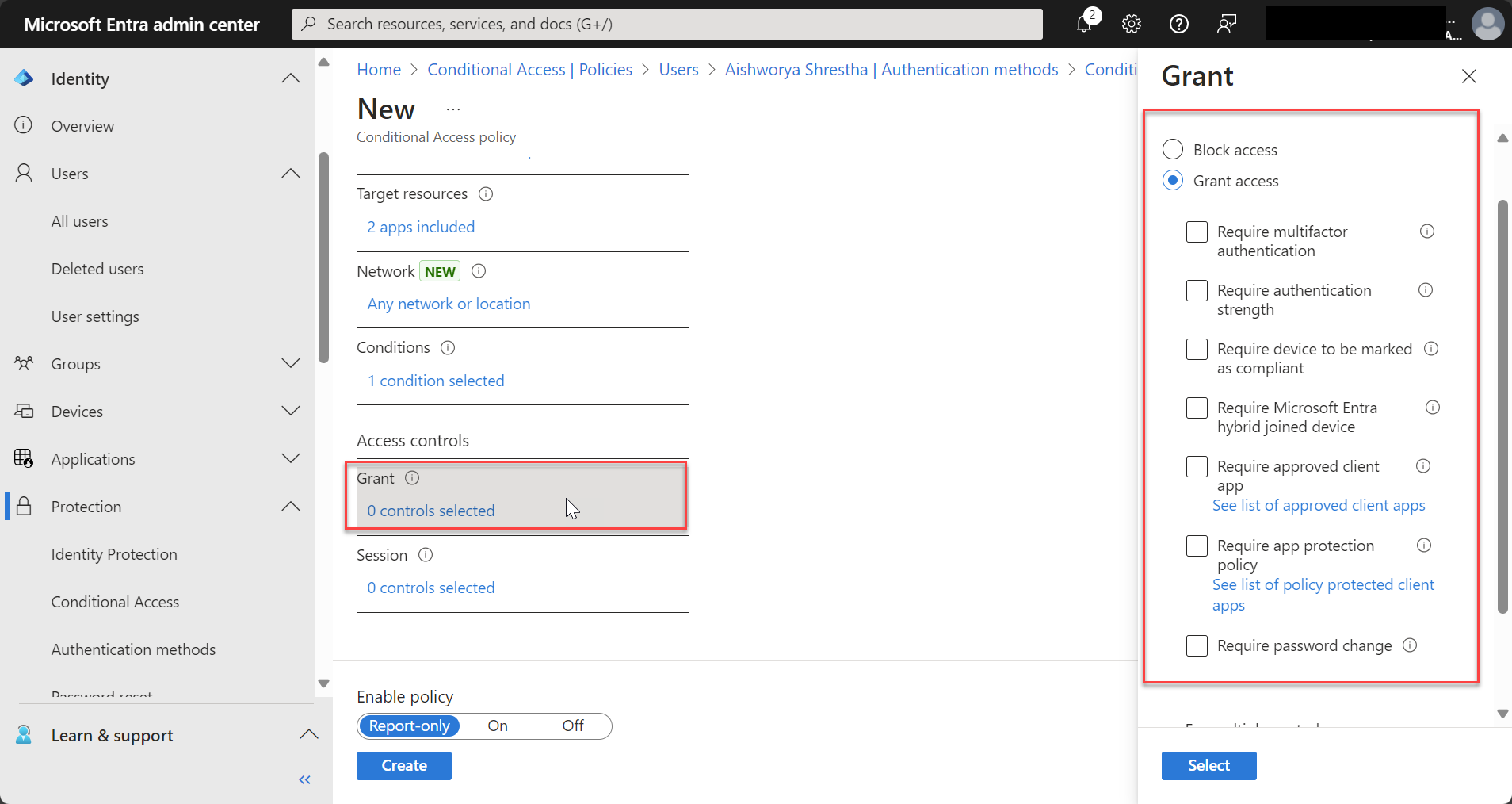
- Block Access: Block access entirely based on risky conditions (e.g., untrusted locations, compromised credentials).
- Session Controls: Manage access duration, app behavior, or control data access within the session. Although, I haven’t select anything on the session.
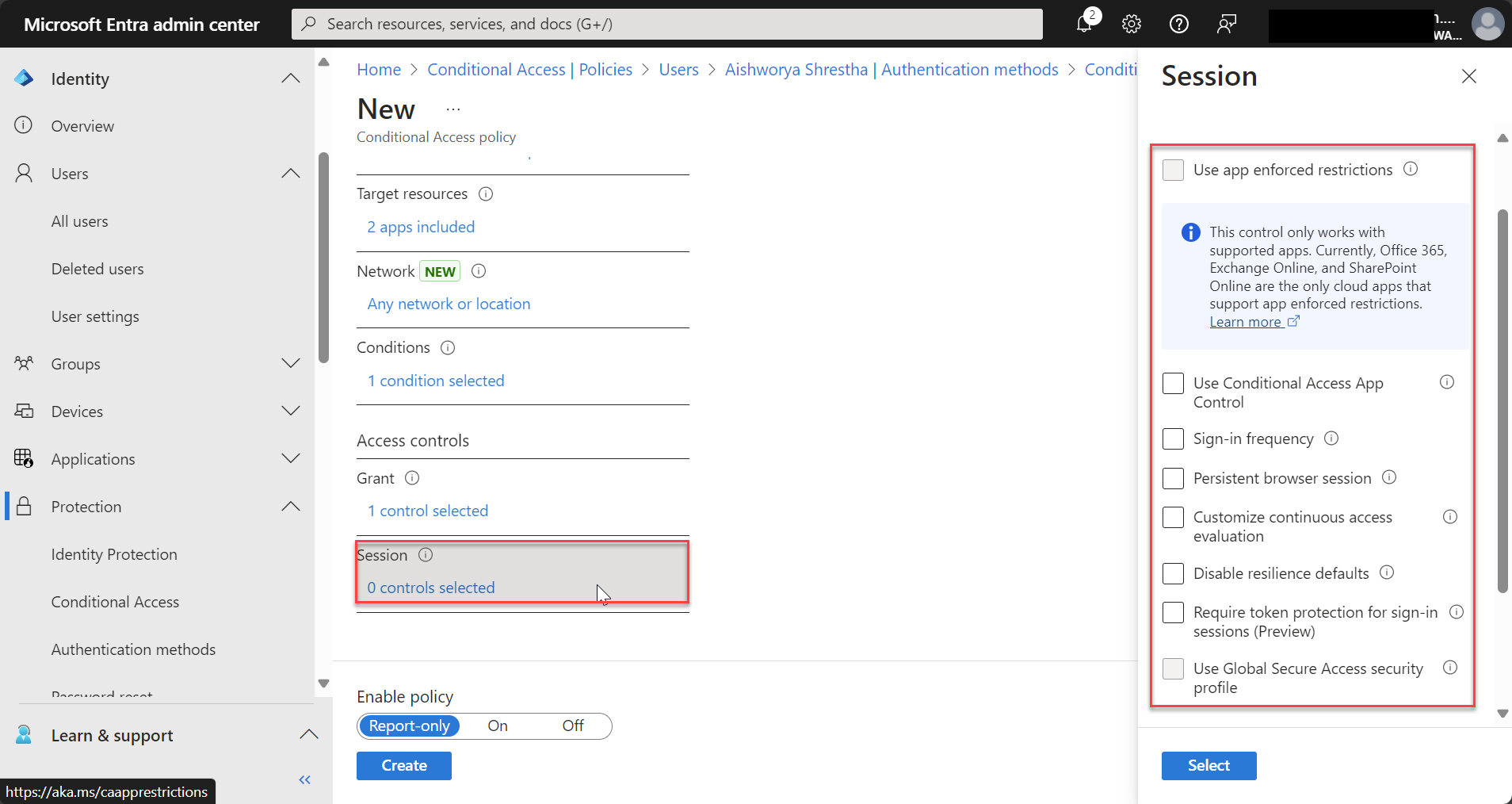
Step 6: Use Report-Only Mode (Optional)
You can enable report-only mode to monitor how the policies would be applied without enforcing them. This lets you test the impact of the policy before rolling it out broadly.
- In the policy settings, toggle Report-Only mode to see logs of access attempts and policy impact without enforcing the controls.
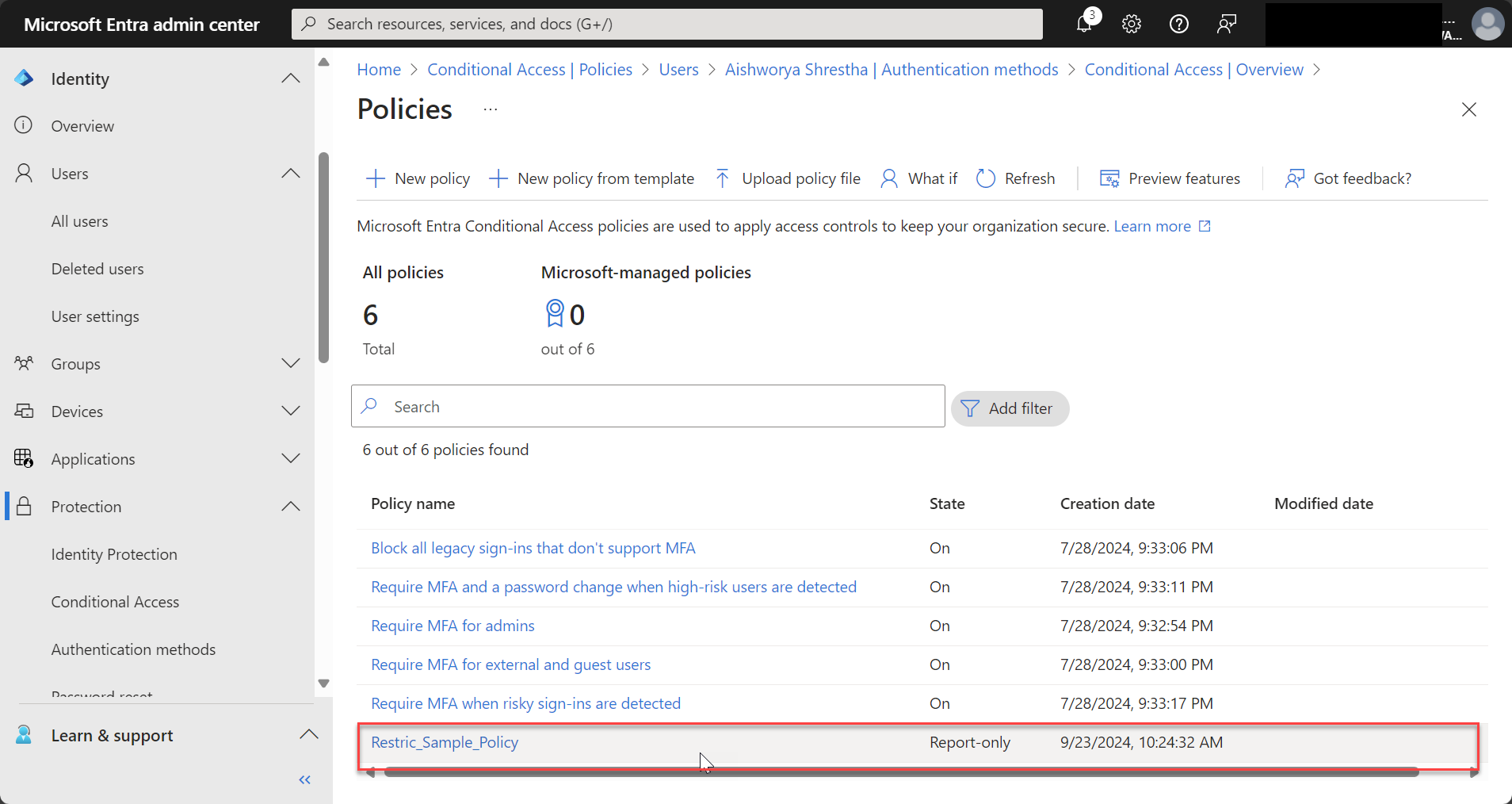
Step 7: Enforce the Policy
After testing in report-only mode, switch the policy to On to start enforcing the controls.
- Ensure that policies are not overly restrictive and allow necessary exceptions for user productivity.
- Regularly review and update your policies to reflect changes in your organization or emerging threats.
Common Use Cases for Conditional Access Policies
1. Enforcing MFA for Remote Workers
Conditional Access can automatically require MFA for users accessing corporate resources from outside the corporate network, securing remote access.
2. Blocking Access from Untrusted Locations
You can block access from high-risk regions or countries known for cyberattacks, ensuring that unauthorized sign-ins from these locations are blocked.
3. Protecting High-Risk Applications
Apply stricter access controls to high-risk apps (HR, finance, etc.), requiring MFA or trusted devices for access.
4. Enforcing Device Compliance
Ensure that only compliant, secured devices (e.g., with the latest security patches) can access corporate resources, preventing access from jailbroken or non-compliant devices.
Best Practices for Implementing Conditional Access
- Start Small: Apply Conditional Access Policies to a small group of users before rolling them out organization-wide to ensure no disruption.
- Use Report-Only Mode: Test your policies in report-only mode to ensure they don’t interfere with legitimate access attempts.
- Implement Layered Security: Use Conditional Access alongside tools like Azure Identity Protection, Privileged Identity Management (PIM), and Azure Security Center for multi-layered security.
- Regularly Review Policies: Review and update your Conditional Access Policies regularly to adapt to new risks and business needs.
Conclusion: Conditional Access for Dynamic Security
Azure Conditional Access Policies are a vital part of any modern security strategy, offering adaptive, real-time controls to ensure that only the right users, on trusted devices, and in secure conditions, can access your resources. By following the step-by-step guide, you can implement Conditional Access Policies that protect your organization from identity-based attacks while maintaining productivity.

